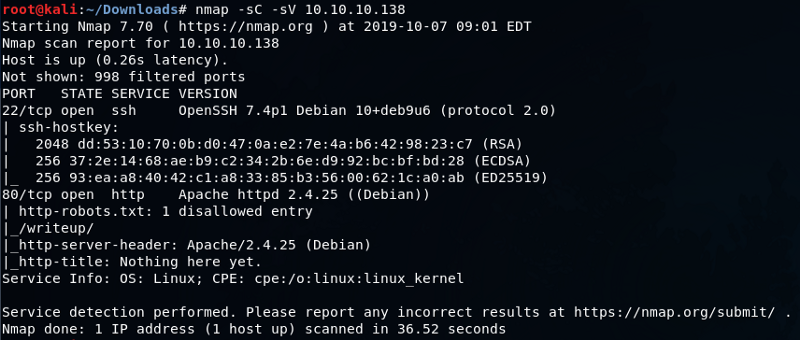
I browsed to http://10.10.10.138/. It was had-crafted with vi.The nmap scan disclosed the robots.txt disallowed entry specifying a directory as /writeup. On viewing the directory /writeup, it had some sample writeups on a couple of htb boxes.On viewing the source code, I found that the web application was using CMS Made Simple as it’s Content Management System.As stated in the source code “CMS Made Simple — Copyright © 2004–2019. All rights reserved.”
Exploitation:
I searched for available exploits for this version.I copied the script to a different directory, opened the script to read it’s contents and found the commands to execute the script.I ran the script. It took some time and I got the credentials.Now, I was able to login via ssh and got the user flag.Next step gaining root.
Privilege Escalation:
I entered the command “id” to get the user information and saw that the user is in staff group.I searched for the staff group debian and got some information from https://wiki.debian.org/SystemGroups. About staff it says,
staff: Allows users to add local modifications to the system (/usr/local) without needing root privileges (note that executables in /usr/local/bin are in the PATH variable of any user, and they may “override” the executables in /bin and /usr/bin with the same name). Compare with group “adm”, which is more related to monitoring/security.
To enumerate the processes I ran pspy in the box and found something similar as stated about the staff group. It took sometime but, I got nothing useful. On logging in via ssh again while running the pspy script I got something useful.The “run-parts” was being executed and the location was not specified in the pspy results.
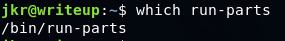
I entered a couple of commands. First to locate the “run-parts” and second, to look for the content of $PATH.Here, the /usr/local/bin is before the /bin, we will able to execute our preferred command by creating a new file named “run-parts” in the /usr/local/bin directory.
I created a simple bash reverse shell script in the run-parts file.I transferred the file to the /usr/local/bin/ directory and created a listener on port 4444.Next step was to login again via ssh so that the run-parts script gets executed. I logged in via ssh and got root access where I had created the listener.
Exploitation:
I searched for available exploits for this version.
Privilege Escalation:
I entered the command “id” to get the user information and saw that the user is in staff group.
staff: Allows users to add local modifications to the system (/usr/local) without needing root privileges (note that executables in /usr/local/bin are in the PATH variable of any user, and they may “override” the executables in /bin and /usr/bin with the same name). Compare with group “adm”, which is more related to monitoring/security.
To enumerate the processes I ran pspy in the box and found something similar as stated about the staff group. It took sometime but, I got nothing useful. On logging in via ssh again while running the pspy script I got something useful.The “run-parts” was being executed and the location was not specified in the pspy results.
I entered a couple of commands. First to locate the “run-parts” and second, to look for the content of $PATH.Here, the /usr/local/bin is before the /bin, we will able to execute our preferred command by creating a new file named “run-parts” in the /usr/local/bin directory.
I created a simple bash reverse shell script in the run-parts file.I transferred the file to the /usr/local/bin/ directory and created a listener on port 4444.Next step was to login again via ssh so that the run-parts script gets executed. I logged in via ssh and got root access where I had created the listener.














Post a Comment