Scanning:
Starting the enumeration using Nmap, we get following results.
Enumerating the website:
When enumerating a web application that has an e-commerce based functionality, there are certain possible vulnerabilities that are associated with it. The methodology to enumerate is to first check for the products that are available to purchase. Focus should be on the parameters and values being sent as request in the URL. Tampering with these parameters will generate responses accordingly. I proceed ahead with enumerating in detailed steps. The vulnerability here is SQL Injection.
Some other details found while enumerating the web application were,
SQL Injection:
My preference was that the exploitation should be completely manual in order to understand the basic SQL Injection methodology. This can be easily cracked using SQLMap and shell can also be accessed from SQLMap itself.
1. Checking the functionality to book rooms.
4. Next task is if I can determine the number of columns. Columns can be multiple as the columns involved in a booking functionality may be for price, name, rating, feature, etc.
Here I can use ' ORDER BY n-- to enumerate the number of columns, where n is the number of column.
When n == 8, the image disappeared, that means the number of columns are 7. One thing to note here is that the single quote before ORDER BY statement was not working here.
5. Now proceeding ahead with UNION SELECT statement to determine the column that contains useful data. The web application may respond with our supplied SQL injection to determine critical information.
6. I was not able to retrieve anything. This is because the parameter value being sent is 3 that is a valid value in the app functionality. Replacing 3 with 0 results in a different output.
7. Determining information regarding the SQL database being used. Checking PortSwigger website to get useful SQL statements to determine the SQL database.
8. Determining more information from the SQL database. I moved ahead with cheat sheet provided for MariaDB database. Checking for MariaDB database cheat sheet, I got PentestMonkey provided detailed SQL statements for the same.
9. Determining user.
Current User SELECT user();
User name is DBadmin.
10. Determining password. This part required a bit of researching on how to get useful data by combining all values and get there output at the same time because if we try to provide multiple statements in 2nd column then no useful information is provided.
11. To overcome this issue we required a SQL statement that works similar to the UNION SELECT statement. The given link helped.
12. I got the following details.
User : DBadmin
Password Hash : 2D2B7A5E4E637B8FBA1D17F40318F277D29964D0
Gaining Access :
Seeing the password it's actually a password hash that needs to be cracked to get the actual password. Meanwhile I need to bruteforce directory in order to get a login dashboard where I will be using the above credentials.
Gobuster gives the following results. As per the web application it's made using PHP langauge, I used PHP.fuzz.txt from SecLists.
The /phpmyadmin directory :
Using the credentials now, DBadmin as user and imissyou as password, I got logged in.
Gaining Shell :
Searched for the given version of phpmyadmin 4.8.0 for possible exploits available and found one on exploitdb.
Downloaded the script and started working with it.
Gaining the User Flag :
The exploit was successful. Now executing our desired command to get user flag.
Commands are being successfully executed but, not able to print the user flag. This is because we are not authorized as the user pepper to print the user flag yet.
User Privilege Escalation :
Using sudo -l command if there exists any functionality that can be executed at user level without requiring user level password. A file exists.
Checking file contents.
The content of the php reverse shell is given below.
Created python server on my virtual machine.
Uploaded the php reverse shell and moved it to the /var/www/html directory to access it via URL.
Getting reverse shell.
Shell has been obtained. Next step is to check the simpler.py script and see what it actually does.
Modifying the shell using python -c 'import pty; pty.spawn("/bin/sh")'
Looking at the script, found a function where it's written 'ping ' + command and also in forbidden variable declared $ is missing so let's utilize the same and try getting a shell.
Now, try executing the same.
Getting a reverse again.
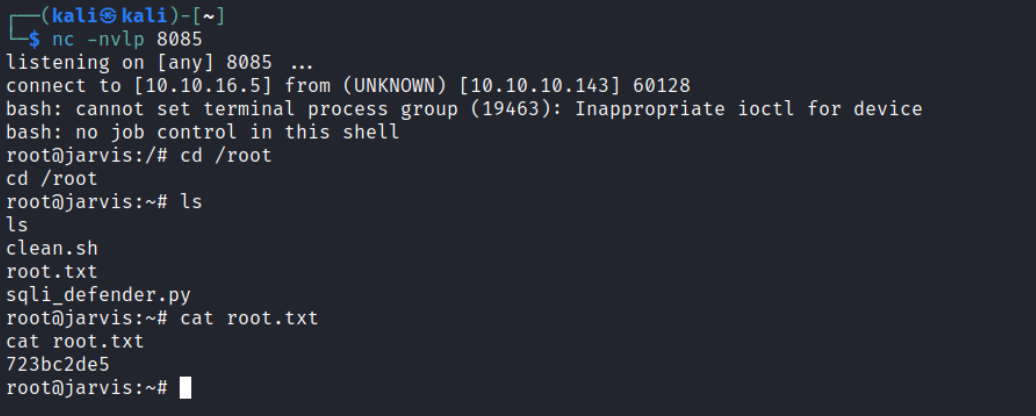
Got it. Checking for the user flag.
Root Privilege Escalation :
Checking using LinEnum script for something I can utilize and gain privilege.
Writing a service and enable using systemctl. This service will contain reverse shell obtaining code. This can be found on GTFOBins.
Uploading the service on the target machine.
Getting the reverse shell.






































Post a Comment